IDSTower
IDSTower can use the VulnCheck Initial Access Intelligence API as a source of Suricata rules.
Setup Instructions
The following instructions were developed against IDSTower 2.7.2.
- Log into the VulnCheck Dashboard and click on User Icon > Tokens.
- Click Create Token to generate a VulnCheck new token to use with IDSTower.
- Log into the IDSTower Dashboard and click on Settings in the left-hand side menu.
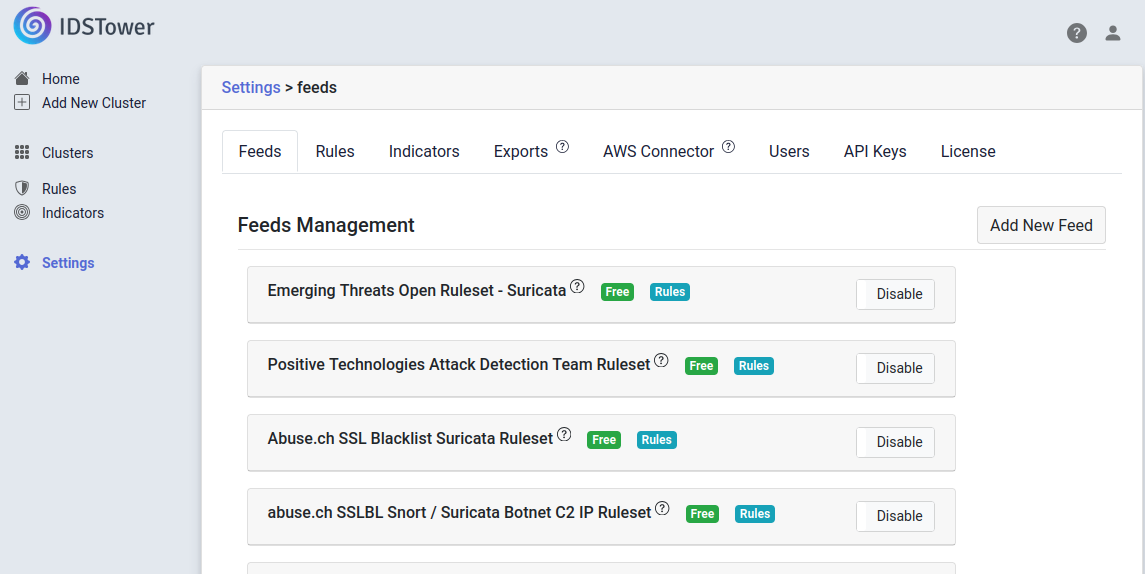
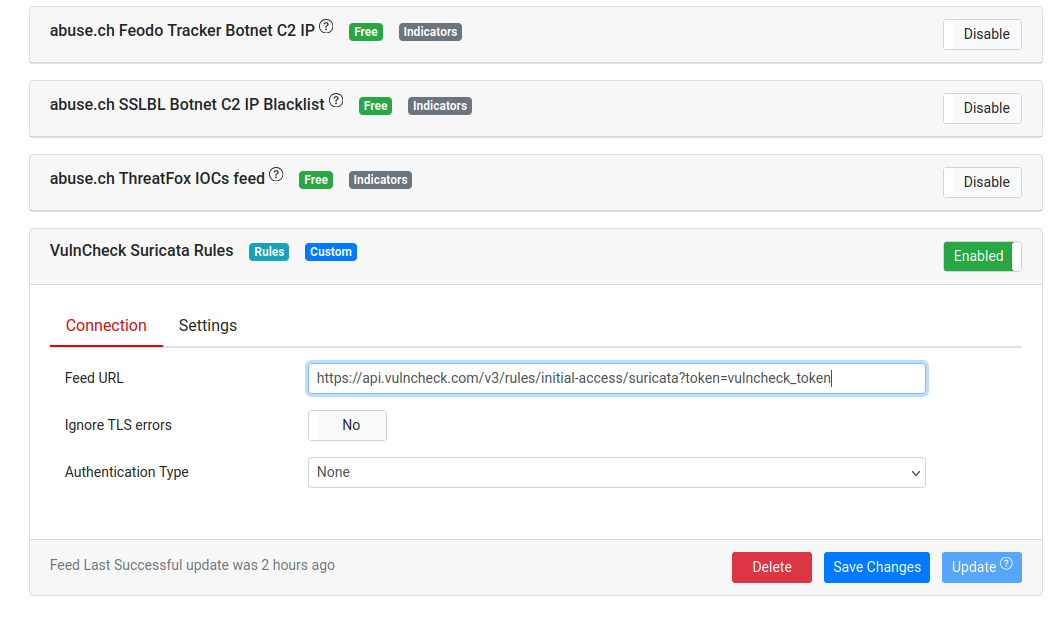
- On the Settings > feeds page, click the Add New Feed button on the right.
- Set the Feed URL to
https://api.vulncheck.com/v3/rules/initial-access/suricata?token=vulncheck_TOKENwherevulncheck_TOKENis the token you created in Step 2.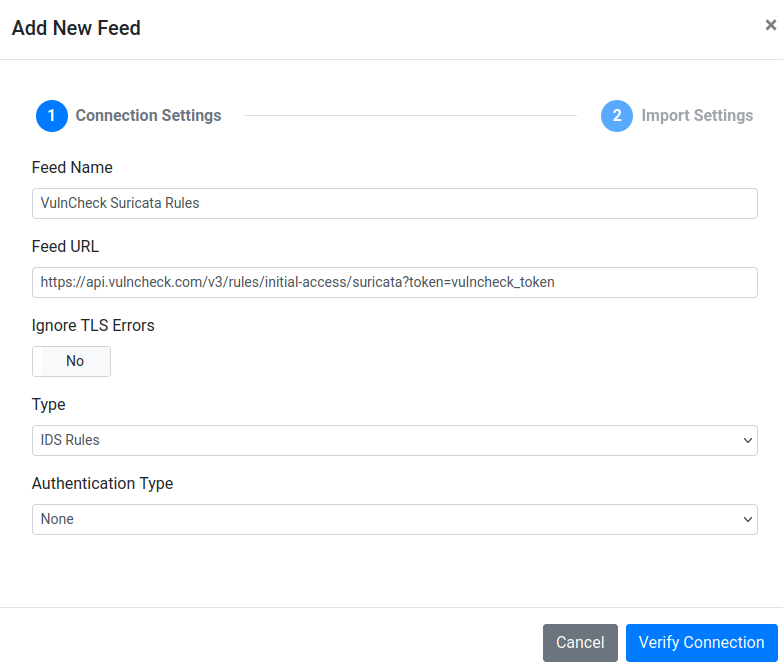
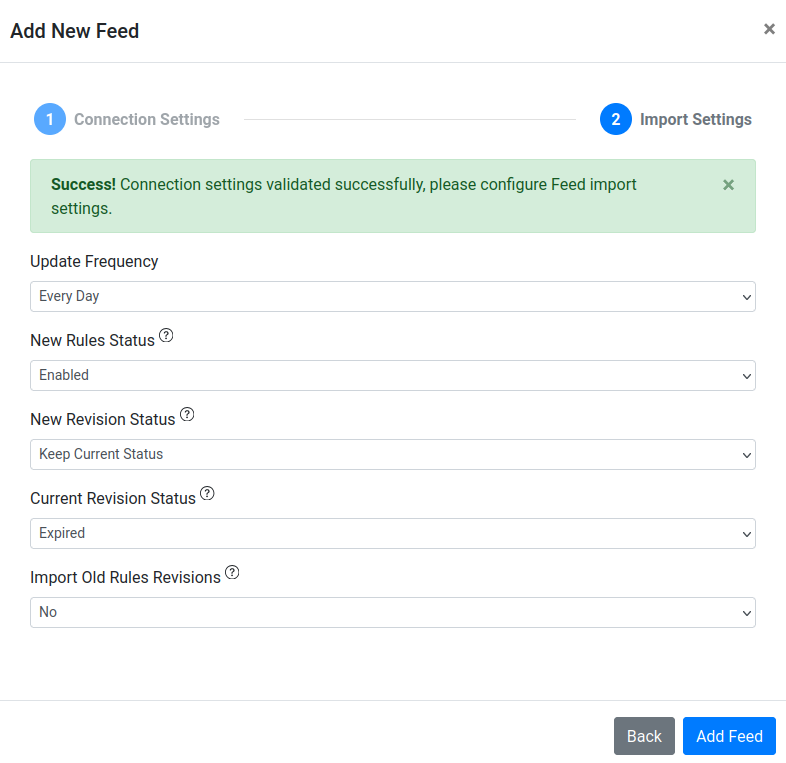
- Click the Verify Connection button. This should transition you to the following screen with a message indicating that the connection was succesful. Click Add Feed.
- There should now be a VulnCheck drop down in the Settings > Feeds tab, likely as the last entry. Click the Update button.
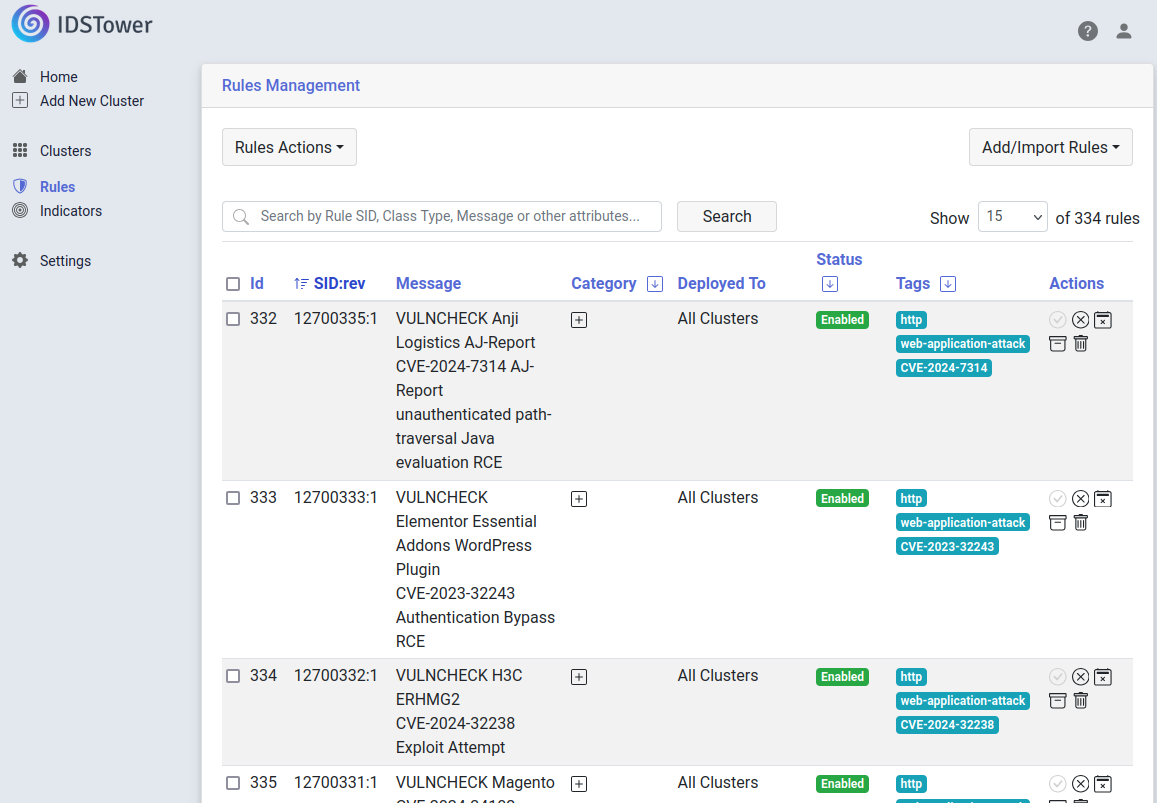
- The VulnCheck Suricata rules should now be available in the Rules Management view.